This article describes support for MSIX Package Signing by TMEditX when using the new DigiCert KeyLocker Code-Signing service. It will be included in version 3.4 of TMEditX.
Until recently, you had three choices when it came to the signing of your MSIX packages:
- Create your own free private certificate, suitable when packages are only distributed for consumption inside your own organization. This produces a password protected PSF file that you use.
- Purchase a code signing certificate from a public Certificate Authority. This prevents the need to install the certificate on end-user devices and allows for external use of the package (such as for customers or contractors).
- Use Device Guard V2 signing via Azure. Also free, mainly for use in your Azure tenant. There are known issues with multiple regions. Here, you never touch the actual certificate.
Due to problems with large software providers that lost control of their public code signing certificate, the industry is moving to new standards for the storage of the certificates. DigiCert has an article explaining these new requirements New private key storage requirement for Code Signing certificates (digicert.com)
These changes do not affect (at least for now) how you would create/protect/use a private code signing certificate, but new certificates from public CAs need to meet the new standards, and Microsoft appears to be closing down Device Guard signing in favor of a new Azure Code Signing service that is currently in private preview mode (GA date is uncertain but I hear that Microsoft has already stopped accepting new Device Guard Certificate service setup requests).
It is unfortunate that these new standards will complicate our use of code signing certificates, but we’ll have to live with it.
The new standards require that certificates be stored in a secure location; generically we can say this means an HSM device or service.
DigiCert started issuing certificates on June 1 that meet the new standards. They offer two choices when buying or renewing your certificate. You can store on a FIPS 140-2 level 2 compliant HSM based storage (and they will sell you a compliant USB token for $150 or you can use your own), or you can use their KeyLocker cloud-based service (which also has an annual storage fee for the cert that isn’t so well documented at present).
To use an HSM device, it needs to be present on the VM where signing is being performed. This isn’t necessarily convenient for automation or remote VMs. The use of the KeyLocker service may be automated.
To use the KeyLocker service, see the DigiCert documentation for all the details (DigiCert KeyLocker), but here is what you’ll do to get set up.
- You request that your DigiCert account add the KeyLocker Service. This seems easiest done by purchasing a certificate to be stored there and then adding a note to the technician to add the service to your account.
- Add appropriate user accounts to the KeyLocker service.
- Get the DigiCert ONE API Key.
- Install some DigiCert provided tools on the signing VM.
- Add the path to smctl.exe to the system PATH variable.
- Authenticate with the service and create a client certificate for your device.
- Store the client authentication certificate in the windows certificate store.
- Create a keypair alias on the service that authorizes signing for that key from this device.
- Run “smctl.exe healthcheck” from a command line to prove that you are ready to go.
To use KeyLocker in TMEditX, you will need to enter some information into the Options page. Normally the page would look something like this:
Change the Signing Method to DigiCert Keylocker, type in the keypair-alias and click the button to extract the subject field out of the associated certificate. This value will be placed in the Subject field below and used to update the Publisher field of the manifest.
Don’t forget to click the Apply button on the bottom of the page to save these settings!
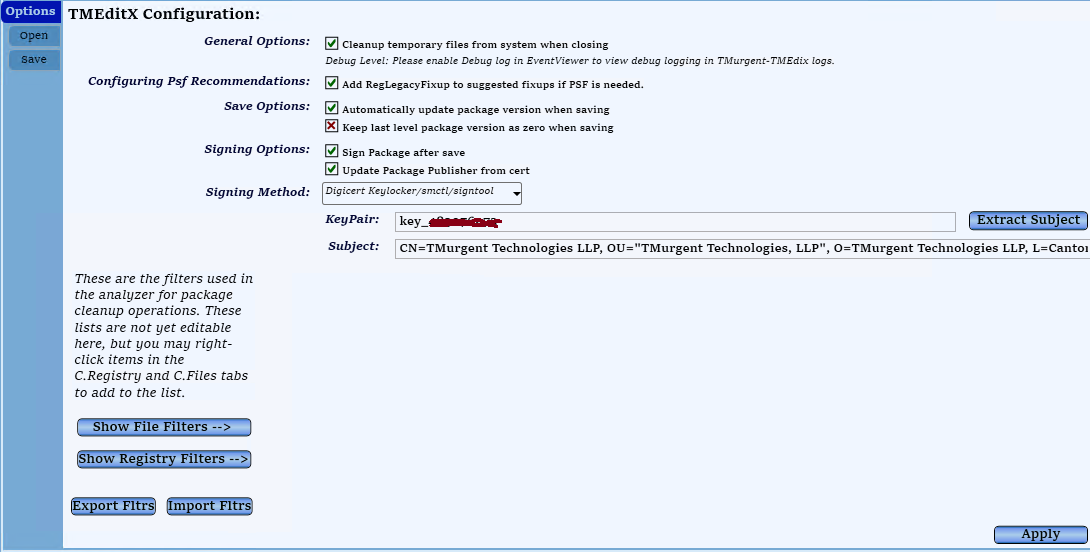
With these settings in place, when you save the MSIX package TMEditX will:
- Update the Publisher field to match the subject field of the package.
- Optionally increase the package version number.
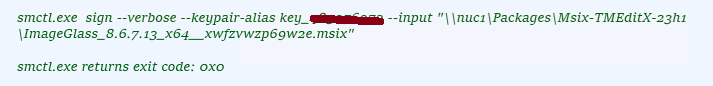
- Use smctl.exe from the DigiCert Tools to communicate with the service and then use signtool to sign the package using new extensions that Microsoft added. It will also timestamp the signing using the DigiCert timestamping service.
You can see this in the output after signing:
NOTE: The new Azure Code Signing service will also require a special setup when added to TMEditX as a third signing method. We are not only waiting for GA of that service, but there may be some additional support we are requesting to be added, so that you don’t have to type in the Subject field.